The Yaxa Analysis Engine utilizes unique reinforced ML to monitor user traffic accessing critical web applications building a unique profile for each user’s behavior. It extracts, analyzes, and builds behavioral profiles from live data packets and captures identity information from existing IAM servers. We prevent loss of valuable data by following a “trust but verify approach,” with minimal IT intervention. This is done via a robust four-step process:
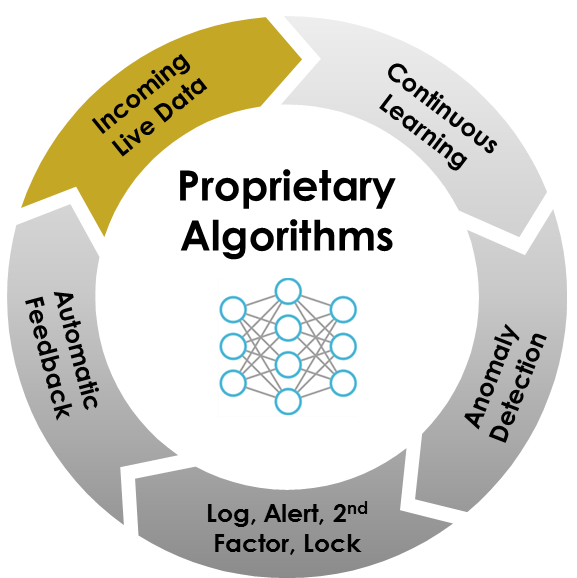

YAXA enables user and application specific access controls. User behavioral traits such as; time and duration of access, speed, geolocation, user agent, client device, response types, application zones accessed, sequence of operations, upload and download behavior to build a deep behavioral model of all users accessing your web-based applications. Yaxa’s behavioral fingerprinting is the first process in protecting your valuable assets. No more fine tuning of static rules.

Our dynamic behavioral fingerprinting process automatically establishes user baseline from which YAXA detect real-time anomalies as the users or devices access the assets under protection. Yaxa employs an ensemble of advanced machine learning algorithms developed in collaboration with a top technology university. The ensemble method boosts accuracy of anomaly detection maximizing coverage of user or devices behavior and minimizing false alerts.

Upon detecting an anomalous session, Yaxa’s automated Incident response mechanism triggers an authentication request to vet the user in real-time. Flexible policy allows administrators to customize profiles based on perceived threat, risk sensitivity, and user privileges. YAXA can distribute an authentication request to an individual user, manager or multiple persons based on company policy.
Yaxa constantly incorporates user feedback into behavioral models in order to adapt to changing user behavior and risk patterns. With such unsupervised and adaptive learning, Yaxa is able to reduce future alerts while responding to ever changing threat landscape.
Real time
Rather than rely on forensics and retrospective analysis, Yaxa provides automated incident response to thwart an insider attack once detected.

Beyond perimeter defenses
Firewall /IPS/ IDS, being signature-based solutions designed to keep attackers out of the network, cannot deal with Insider threats which only Yaxa can combat successfully.
Effective against Zero-Day Vulnerabilities
Yaxa solution is identity aware and uses advanced Machine Learning algorithms to detect hitherto unknown vulnerabilities.
Flexible deployment
The Yaxa appliance can be deployed either in Data-Centre or in the Cloud.

Monitors the network traffic and leverages Big Data
Yaxa collects and analyses packet headers/meta data as it monitors HTTP/HTTPS traffic and indexes the data to make it more easily and efficiently searchable for various decisions.
Eliminate false alarm
Yaxa reduces the need for IT intervention manually by taking corrective action automatically upon anomaly detection and policy violation.



Human attack surface by 2021
Average security alerts per day

Percent of network traffic is encrypted

Yaxa can provide a demo for your custom/internal application or SaaS applications like SalesForce, Office365, DropBox, Gmail, Box and other web based applications.